Study of IT security in 2025
IT experts assume that cyber attacks will primarily target the Internet of Things and production system controls in future, as a current industry study reveals.
What will IT security look like in the year 2025? This question was the focus of a study conducted by RadarServices. The Funk cooperative partner surveyed 105 IT security experts from 25 countries in Europe and Asia about IT security and the digital threat of tomorrow. The most important results:
Companies are ill-equipped
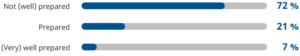
The vast majority of companies are not sufficiently prepared for the future, according to 72% of the respondents. Operating on a scale of 0 (not prepared) to 10 (very well prepared), only 7% of respondents indicated that they were well or very well prepared for threats of the future.
Cyber attacks will ramp up dramatically
On average the expected annual growth rate is 300%. Around a quarter of respondents even thought a cyber attack increase of 500% to 1,000% was likely. A further 7% estimate the growth to be even higher.
Just under 30% thought an increase between 100% and 500% per year was realistic. Not a single one of the 105 IT experts surveyed thought cyber attacks would decrease or stay the same over the coming years.

Internet of Things and infrastructure will be the focus of attacks
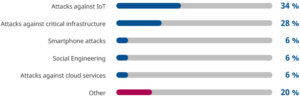
The experts primarily consider attacks on the Internet of Things (IoT) and critical infrastructure, such as production system controls, to be the greatest problem of the future. Also relevant: attacks on smartphones and cloud services.
How companies can protect themselves
To provide companies with optimal support in identifying and protecting themselves against cyber risks, Funk and RadarServices offer the comprehensive cyber risk analysis. This analysis comprises a business part, which points out the potential risks and determines the consequences for value creation, and a technical security analysis, which provides an overview of the vulnerabilities in a company’s IT landscape. Learn more about it in our article on cyber risk management.



